This is just Task 5 & 6, because those ones were fun for me. I did this on my own VM of Kali and therefore may be different if you use the TryHackMe attackbox.
Task 5: Password Cracking
First step for me was to look up the wordlist and I’m glad I did, because rockyou was zipped.
I used the following to unzip the file in: /usr/share/wordlists/
sudo gzip -d rockyou.txt.gzNow that is done we will proceed with the question at hand:
Q1: Crack this hash: $2a$06$7yoU3Ng8dHTXphAg913cyO6Bjs3K5lBnwq5FJyA6d01pMSrddr1ZG
Let’s put this in a file:
echo '$2a$06$7yoU3Ng8dHTXphAg913cyO6Bjs3K5lBnwq5FJyA6d01pMSrddr1ZG'> hash.txt
Look at the prefix. This means the hash type is bcrypt. Notice we added the ‘ to the front of the string and we added ‘> to the end of the string. Next, run this command:
john hash.txt --format=bcrypt --wordlist=/usr/share/wordlists/rockyou.txtA1: 85208520
This is fun let’s do another…
Q2: Crack this hash: 9eb7ee7f551d2f0ac684981bd1f1e2fa4a37590199636753efe614d4db30e8e1
Again we put it in a file:
echo '9eb7ee7f551d2f0ac684981bd1f1e2fa4a37590199636753efe614d4db30e8e1'> hash256.txtThis is sha256 so we need to change the format on our command when we run JohntheRipper on it.
john hash256.txt --format=raw-sha256 --wordlist=/usr/share/wordlists/rockyou.txtOur results look like this:
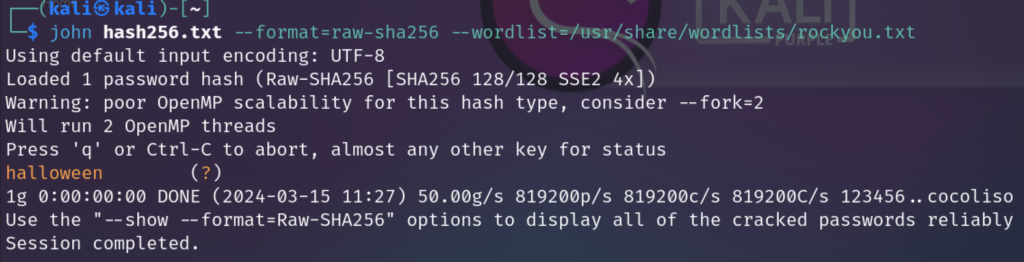
A2: halloween
Q3: Crack this hash: $6$GQXVvW4EuM$ehD6jWiMsfNorxy5SINsgdlxmAEl3.yif0/c3NqzGLa0P.S7KRDYjycw5bnYkF5ZtB8wQy8KnskuWQS3Yr1wQ0
This one is sha512crypt so we will change our format in the following command, but first we create our file:
echo '$6$GQXVvW4EuM$ehD6jWiMsfNorxy5SINsgdlxmAEl3.yif0/c3NqzGLa0P.S7KRDYjycw5bnYkF5ZtB8wQy8KnskuWQS3Yr1wQ0'> hash512crypt.txt
john hash512crypt.txt --format=sha512crypt --wordlist=/usr/share/wordlists/rockyou.txt
A3: spaceman
Q4: Bored of this yet? Crack this hash: b6b0d451bbf6fed658659a9e7e5598fe
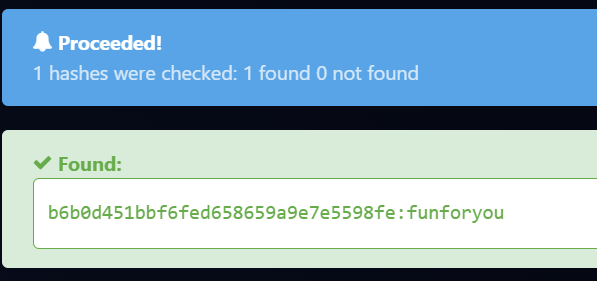
This is Md5, but using rockyou won’t work. The hint says use the internet. So, using https://hashes.com/en/decrypt/hash, we find:
A4: funforyou
Task 6: Hashing for integrity checking
Q1: What’s the SHA1 sum for the amd64 Kali 2019.4 ISO? http://old.kali.org/kali-images/kali-2019.4/
Download and open the first file. The answer is on the first line:
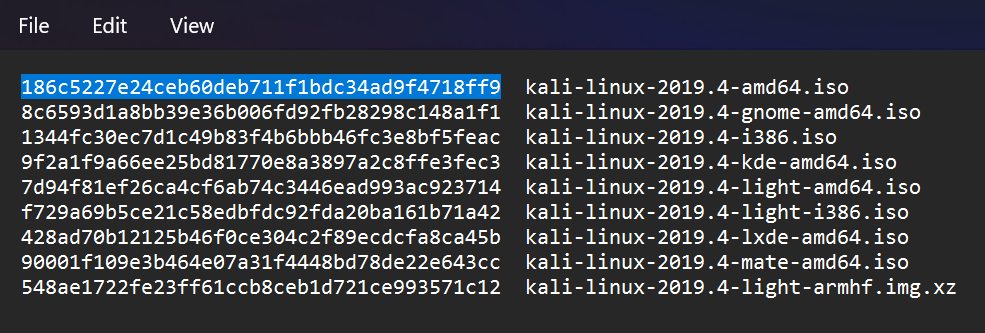
A1: 186c5227e24ceb60deb711f1bdc34ad9f4718ff9
Q2: What’s the hashcat mode number for HMAC-SHA512 (key = $pass)?
Go to the website in the hint: https://hashcat.net/wiki/doku.php?id=example_hashes Do a find on “HMAC-SHA512” and you should find the answer:
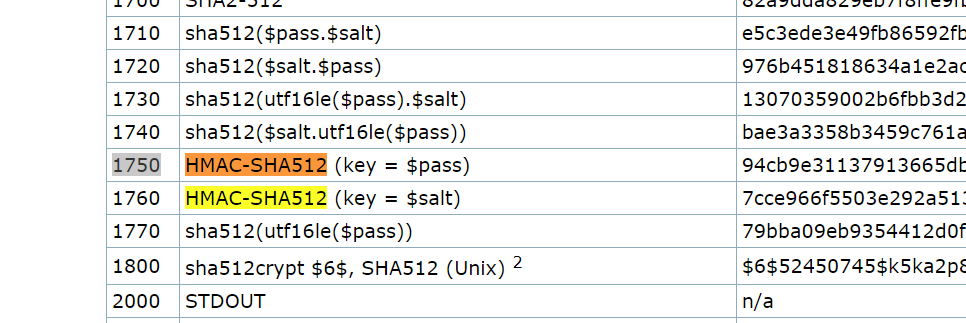
A2: 1750
