Welcome to my weekly cybersecurity roundup! Here, I share updates on the projects I’m currently working on, along with the most insightful cybersecurity videos I watched, articles I found valuable, and podcasts I tuned into this week.
Featured article analysis
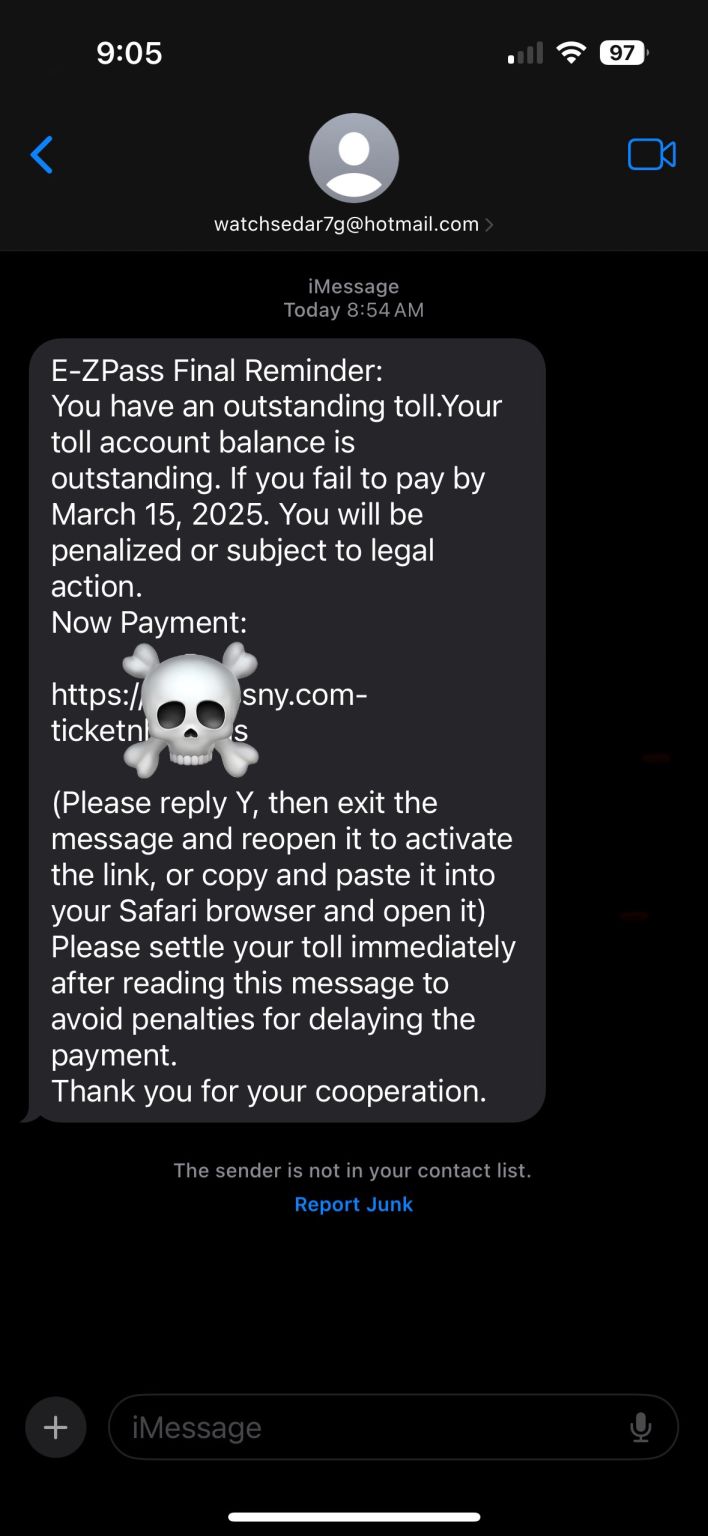
This weeks feature article analysis is from: https://www.bleepingcomputer.com/news/security/toll-payment-text-scam-returns-in-massive-phishing-wave/
This recent E-ZPass smishing campaign highlights several evolving tactics cybercriminals are employing to bypass security measures and exploit user trust. The attackers leverage high-volume, automated messaging systems originating from seemingly random email addresses, a method designed to circumvent standard carrier-based SMS spam filters that primarily target phone numbers. By impersonating official bodies like E-ZPass or the DMV and instilling a false sense of urgency with threats of fines or license suspension, they effectively employ social engineering. A particularly noteworthy technique involves instructing users to reply to the message, cleverly bypassing Apple iMessage’s built-in protection that disables links from unknown senders. This user interaction effectively marks the malicious sender as “known,” activating the phishing link and demonstrating how attackers exploit platform features and user behavior in tandem.
The sophistication extends beyond the delivery mechanism, with the phishing landing pages themselves designed to appear legitimate and, significantly, often configured to load only on mobile devices, evading desktop-based security analysis. The sheer scale suggests the involvement of organized operations, potentially utilizing Phishing-as-a-Service (PaaS) platforms like the mentioned Lucid or Darcula. These services specialize in abusing modern messaging protocols like iMessage and RCS, which offer end-to-end encryption and different delivery paths, making detection harder and campaign execution cheaper than traditional SMS. This underscores the ongoing challenge for defenders: attacks are becoming more targeted, evasive, and leverage platform-specific features, necessitating continuous user education (don’t click, don’t reply, verify independently) alongside technical defenses and prompt reporting to platforms and authorities like the FBI’s IC3.
Projects
- TryHackMe – Networking Core Protocols – Complete
- TryHackMe – Networking Secure Protocols – In Progress
Videos
Articles
- Twitter (X) Hit by 2.8 Billion Profile Data Leak in Alleged Insider Job – Massive Twitter (X) profile data leak exposes details of 2.8 billion users; alleged insider leak surfaces with no official response from the company.
- Fake Snow White Movie Torrent Infects Devices with Malware – Disney’s latest Snow White movie, with a 1.6/10 IMDb rating, isn’t just the biggest flop the company has ever released. It’s such an embarrassment that the movie isn’t even available on Disney’s own streaming platform, Disney+.
- T-Mobile Coughed Up $33 Million in SIM Swap Lawsuit – T-Mobile paid $33 million in a private arbitration process over a SIM swap attack leading to cryptocurrency theft.
- FBI and DOJ seize $8.2 Million in romance baiting crypto fraud scheme – The U.S. DOJ seized over $8.2 million in USDT stolen through ‘romance baiting’ scams, where victims are tricked into fake investments promising high returns.
- OpenAI just made its first cybersecurity investment – Generative AI has vastly expanded the toolkit available to hackers and other bad actors. It’s now possible to do everything from deepfaking a CEO to creating fake receipts.
- UK’s attempt to keep details of Apple ‘backdoor’ case secret… denied – Last month’s secret hearing comes to light
- Food giant WK Kellogg discloses data breach linked to Clop ransomware – US food giant WK Kellogg Co is warning employees and vendors that company data was stolen during the 2024 Cleo data theft attacks.
- Google Pushing ‘Sec-Gemini’ AI Model for Threat-Intel Workflows – Experimental Sec-Gemini v1 touts a combination of Google’s Gemini LLM capabilities with real-time security data and tooling from Mandiant.
- A member of the Scattered Spider cybercrime group pleads guilty – A 20-year-old man linked to the Scattered Spider cybercrime group has pleaded guilty to charges filed in Florida and California.
- Oracle privately notifies Cloud data breach to customers – Oracle confirms a cloud data breach, quietly informing customers while downplaying the impact of the security breach.
- Expert used ChatGPT-4o to create a replica of his passport in just 5 minutes bypassing KYC – A researcher used ChatGPT-4o to create a replica of his passport in just five minutes, realistic enough to deceive most automated KYC systems.
- 39 Million Secrets Leaked on GitHub in 2024 – GitHub has announced new capabilities to help organizations and developers keep secrets in their code protected.
- North Korea’s IT Operatives Are Exploiting Remote Work Globally – The global rise of North Korean IT worker infiltration poses a serious cybersecurity risk—using fake identities, remote access, and extortion to compromise organizations.
- One of the last of Bletchley Park’s quiet heroes, Betty Webb, dies at 101 – Tip-lipped for 30 years before becoming an ‘unrivaled advocate’ for the site